Blog
In our blog posts and video formats, we explain everything you need to know about IT security – in easy-to-understand language.
Hacker protection: This is how IT logins must be done in companies in 2025
15.11.2024

Improved Phishing Awareness Campaigns with Lucy Security
14.10.2024

Security Operations Center (SOC) for companies: What you need to know
11.06.2024

AI in Cybersecurity: Risk or Benefit?
28.05.2024

Trufflepig expands into Switzerland with new location
24.04.2024

Top 5 Hacker Attacks 2024: Trends and Countermeasures
26.03.2024

Prove Insider Data Theft: Forensic Experts Reveal How
04.03.2024

THE 5 BIGGEST PHYSICAL IT RISKS AND HOW TO PROTECT YOUR BUSINESS
26.02.2024

The danger of hacker attacks: What threatens your company
23.02.2024
Common Backup Mistakes: How to Protect Your Data and Ensure Recovery
21.02.2024

Cybersecurity Trends 2024: What to Expect
06.02.2024

After the risk analysis: systematically protect IT from hacker attacks
22.01.2024

Ransomware attack: How to minimize the damage
11.01.2024

Phishing: Training employees with real attacks
10.01.2024

Ransomware attack: should you pay?
08.12.2023

Trufflepig supports AI-powered cybersecurity project (CAIDAN)
17.11.2023

How a small phishing email became a ransomware attack in an educational organization #case-report-1
08.11.2023
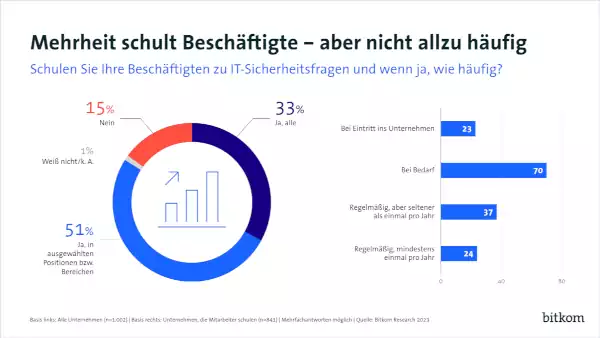
BITKOM Study: Closing the Cybersecurity Training Deficit
07.11.2023

Incident response: What to do when you're hacked
27.10.2023

The true cost of a ransomware attack
25.10.2023

Cyber Insurance for Businesses: What Companies Need to Know
20.10.2023

Avoid corporate liability in the event of hacker attacks
09.10.2023

How to recognize a hacker attack and react correctly in a company
18.09.2023

Phishing – An overview of the most important information
13.09.2023

Fast Cyber Risk Analysis: Get Your IT Security Assessment in Weeks
25.08.2023

Ransomware: What you need to know
18.08.2023

Key Findings from the Public Sector Pentest
31.07.2023

IT forensics: What business owners need to know
12.07.2023

How companies protect themselves from hacker attacks
11.07.2023
Valuable information on "IT security" once a month via Newsletter